My experience as a parent, uncle, and ex child is that kids love playing games. This page is all about hosting murder mystery games for your kids. And to be honest, the interactive murder mystery games I talk about here bring out the kid in me. not just for grown ups. Some of these party games are a bit different to the other games on this site. Theyre not all interactive murder mystery games I hope you like the wider choice. Just to let you know that my daughter played Curse of the Pharaoh with 9 other girls for her 1. We havent done anything like this before and admittedly it was quite a complex plot for a first attempt However everyone loved dressing up especially dressing as men and they all had a great time. Thought youd welcome the feedbackThanks very much. From Liz Marshallhosting a game for kids. Based on my experience of running murder mystery games for kids and Im not an expert by any imagination, here are a few things to look out for. Lots of introductory blub Some games including the Freeform Games parties provide a fair amount of pre party information, including the invitation, a background newsletter and other things. Dont expect kids to read much more than the invite and even then, not a lot of that. A longer introduction may be needed As a result of kids not wanting to read anything beforehand, you may need a longer introduction. So you may have to take longer to set the scene and go through any rules. That, however, is balanced by the next point. A shorter running time If my experience is anything to go by, an all kid group will blast through plots and secrets and will probably finish in a much shorter time than you might otherwise have expected. Shyness Kids can be shy I know I was and dont like looking like idiots in front of their peers. So as a host you may find that the first part of a game consists of you answering their personal queries privately. Four years makes a lot of difference You may find that some older teens are too self conscious to get fully into the game while 1. Theres also a big difference between a 1. That means that birthday parties might be the best place to run a murder mystery game as all the kids are likely to be more or less the same age. Friends Where possible, cast real life friends as friends in game. Playing with grown ups The easiest way to play with kids is to just incorporate them in the regular murder mystery parties described elsewhere on this site. Although there are often younger characters in the games, you might want to vet them first to ensure that they are suitable. This works really well when you have only one or two kids, but is a little trickier when you have more kids than grown ups. In that case you may need to consider your casting choices carefully you may want to pair up kids and their parents or choose one of the options below. Way out West is an interactive murder mystery game set in Cactus Gulch, a small town in Americas Wild West. Way out West is for 1. Set in Cactus Gulchs saloon, Way out West features land disputes, cowboys and lawman, disreputable card games, strange folk from out of town and hostile Indians. Freeform Games wrote Way out West as a family friendly game to start with, but theyve had a good deal of feedback from people whove run it for groups of kids and younger teens, for birthday parties and the like. So theyve now written a version of the game specifically for kids, and theyre giving it away free with the standard game Click here to discover more about Way out West. These three games are slightly different theyre not murder mystery parties but are instead themed interactive parties that last about an hour and are suitable for including into a larger party. Check out Murder Mystery 2. Its one of the millions of unique, usergenerated 3D experiences created on Roblox. To get the FREE RAINBOW KNIFE EFFECT, click the. Download murder mystery party games to play at your next event for 10100 guests. Many themes for all ages. Just download kit, print host party A gangsterthemed murder mystery party set in a speakeasy in the 1920s. 618 suspect versions available, can accommodate an unlimited number of players. Host a fun murder mystery party. We have murder mystery party games for all ages and group sizes from 5 to over 200 guests. Download this murder mystery party kit about a murder at an NYC cocktail party and have a great evening with your friends. An entertaining cluebased murder mystery party for 610 guests ages 13 up in a traditional old mansion setting. This game has a victim known prior to the game and. In Pirate Island, pirate ships have gathered off a small Caribbean island to take part in the Pirate Games and quest for treasure. Whoever wins the most doubloons is the winner In Monster Mash and Trick or Treat, gangs of monsters are competing to see who can become the best monster gang in the haunted county of Hallowshire. The gang with the most gold wins Trick or Treat is the Halloween version of Monster Mash. The party games are for 6 to 2. Theyre all published by Freeform Games. Click here to go to the Freeform Games website and download the free intro pdf to learn more about Pirate Island. Or click here to download the free intro pdf and learn more about Trick or Treat. Or click here to download the free intro pdf and learn about Monster Mash. Hollywood Lies is an interactive murder mystery game for 1. Hollywood. Dazzled to Death has swept the board at the Eric Awards ceremony and it is now the time of the post awards party. However, Dazzled to Deaths leading actor has been killed is it murder As well as solving the murder, Hollywood Lies includes a movie making game there are three producers who need to make their movie.  Each movie needs a screenplay, actors and a director and the cast and crew of the movie act out a scene from that movie. Hollywood Lies is suitable for older kids aged 1. Halloween Lies is the Halloween version of Hollywood Lies. The two games are the same, but Halloween Lies has a horror movie theme. Click here to learn more about Hollywood Lies. Click here to learn more about Halloween Liesthe birthday party games lady. The Birthday Party Games Lady provides downloadable party games some of them mystery parties, some of them more traditional for kids of varying ages. The games include Medieval Madness a whodunnit for 6th graders. Search and Riddle a detective mystery for 9 1. Survivor a survival game for 6 8 year olds. Harry Potter play Quidditch at Hogwarts for 8 to 1. Not just birthday party ideas complete kids birthday party games packages click here to go to The Birthday Party Games Ladys site and learn more. Mysteries on the Net produce games where the emphasis is on solving the murder. While their adult games can be quite fiendish their kids games are much simpler. In all their games a few kids play the suspects, while the everyone else is a private detective trying to solve the mystery. The Sticky Case of Chuckles the Clown is for 8 to 2. The Curious Case of the Lost Elephant is for 8 to 2. The Mysterious Case of a Quarterback in Space is for 8 to 2. The Hair Raising Case of Rapunzels Green Tresses is for 1. The Perplexing Case of the Pilfered Pooch is for 8 to 2. The Ghostly Case of the Haunted Amusement Park is for 8 to 2. The Strange Case of the Disappearing Presents is a Christmas game for 8 to 2. Click here to go to the Mysteries on the Net site and learn more about their games. Make sure you click on the Looking for a Kids Mystery link when you get to the site. How to Host a Murder Mystery Game. An Evening of Murder, Mystery Mayhem Suddenly the lights go out and you are startled by the sound of a gunshot. Light returns, and you see a dead man on the floor next to you As you look around the room, you notice some very shady characters. One of them must be the murderer, but which one is it This may sound like a movie, but it isnt. You are, in fact, participating in an exciting murder mystery party game. Murder Mystery Parties are becoming a very popular entertainment choice for Party Hosts looking for a unique experience to offer their guests. Party planners want their event to be talked about in excited conversations for weeks afterwards. Your run of the mill food, music and social gathering, just doesnt garner real excitement. Murder mystery games have been very popular in the UK for about 2. Recently, there has been a huge growth of interest in the USA, as more people are becoming exposed to them. The first murder mystery games featured actors who portrayed characters using scripted roles. They would mingle with the guests while dropping clues. These are still performed today at large fund raising events and murder mystery dinner theaters. The next generation of games let the guests themselves play the characters, but the parts were still scripted. Later boxed sets were introduced, which were scripted and played out in rounds, much like a board game. While these could be enjoyable, they lacked spontaneity, or the ability to be creative. Everything went exactly as scripted. Today a new genre of Murder Mystery Games is emerging. These are called Interactive murder mystery games. In the older versions, solving the murder was the sole purpose of the game. Some of the new murder mystery games have many subplots. Guests will have their own nefarious agendas. Parts are no longer scripted. Instead characters receive detailed backgrounds, which describes their fictional relationships with other characters at the party. They also have secrets of their own, which may have nothing to do with the murder that occurs. Participants take on their characters persona. After the murder, they learn certain details of the crime through evidence, eavesdropping, and questioning other characters. Some games include play money, which can be used for buying information, blackmailing, and other devious schemes. All of this leads to extensive social interaction, which is the real point of a party, isnt it How many boring parties have you been to where there were small groups of people gathered together in clusters Or even more horrifying to the hostess, are people standing around, not conversing at all. This just doesnt happen with a well written interactive murder mystery party. With a good game, the guests can get so caught up in their own schemes, that they may even forget to investigate the murder Each murder mystery game usually takes place in exotic locations and timelines. These can include gangsters in Chicago during the roaring twenties, or maybe a sock hop in the fifties. You might even be placed in fictional settings. These settings allow participants to don great costumes and immerse themselves in the setting. This allows guests to more fully experience the ambience of the game. When you decide to host a murder mystery party, there are some things you should look for in the game you choose. First and foremost is to stay away from scripted games. These allow no imagination or spontaneity, and they play more like a board game. For true enjoyment, your guests need to feel immersed in the world your chosen game has created. Look for a theme that you think your guests would enjoy. My best seller is Murder at the Four Deuces, which takes place in 1. Chicago. The reason this game is so successful is very simple, and something many people dont think about. Men are usually the first to balk at participating in this type of event. When told that they will be playing a gangster, they become excited about the idea. It is very easy for men to costume for this theme and they get to play powerful characters. It also allows them and the other guests to be bad, without actually being bad. It is exciting to be able to unleash our normally suppressed tendencies, without suffering any guilt. Something we dont want to do in real life, but relish doing in a make believe way. So, whatever game you do decide on, it is a good idea to choose one with good strong characters for the men. Look for a game that is easy to host. Most of the good games are purchased from the internet. I operated a murder mystery theater before I developed the Dinner and a Murder game system. I know how important it is to be able to have easy to follow instructions. The night of the party, the last thing a hostess needs is to have to scramble around trying to run the game, while making sure all the guests are happy, food is served and cleaning up. You get my point. A good game will have very few hosting duties associated with the game, allowing the hostess to participate as a character also. If the host guide reads like a technical manual move on. Do not purchase a game that does not have an introductory file that you can read before purchasing. All games are not created equal. There are good ones and bad ones out there. You do not want to take a chance on harming your reputation by hosting a bad murder mystery party. If a site cannot give you a partial glimpse of the actual game, then they are very likely hiding something. This introduction should contain the host guide and other details about the game that will give you a good feel for how it will work. While you are at the web site, also look for customer comments. Of course, we all know that they are not going to post negative comments on the site and could in fact make up comments. If you only see one or two line comments, be leery. Customer feedback can also give you great ideas for throwing your own party. I am constantly amazed by my customers creativity. Murder Mystery Game Kit Contents A good kit will have everything you need to play the game. You should not have to go out and purchase elaborate props. It should have invitations, host guide, characters evidence at the least. Game money is a plus that adds a whole new dimension to the game experience. Either the kit, or the web site, should also give you party theme ideas. Everything from menu, recipes, decorations, hairstyles, music and costumes can give a host very good ideas for their party. If your kit does not contain certificates, you can design some yourself. It is always nice to be rewarded in the game for solving the murder, best costume, best performer etc. Next I will give you some tips on planning and hosting a murder mystery party Try to plan your event at least 2 weeks in advance. A month advance planning is most optimal. You can throw a last minute party, but things will be much less stressful with careful planning. Before assigning characters, it is very important to send an invitation and receive an RSVP. Let your guests know that when they confirm, you are counting on them to attend. When it comes to food, easier is better. I have thrown murder mystery parties where I did all of the cooking and it made for a very stressful day and party. Unless you can have your party catered, the easiest menu is done potluck. The first time I decided to do this, I worried about what my guests would think, but to my surprise they loved the idea. It gives them a chance to contribute to the party and show off their culinary skills. Just about everyone has a special dish that they excel at. If not, there are always needed items that dont require cooking skills. Drinks, ice, cups etc. If you do decide to cook, think simple and have everything ready before the party starts. After the solution has been read, it is always fun to go around the room and let each character reveal their secrets. Your guests will be amazed at what they didnt know was going on under their noses.
Each movie needs a screenplay, actors and a director and the cast and crew of the movie act out a scene from that movie. Hollywood Lies is suitable for older kids aged 1. Halloween Lies is the Halloween version of Hollywood Lies. The two games are the same, but Halloween Lies has a horror movie theme. Click here to learn more about Hollywood Lies. Click here to learn more about Halloween Liesthe birthday party games lady. The Birthday Party Games Lady provides downloadable party games some of them mystery parties, some of them more traditional for kids of varying ages. The games include Medieval Madness a whodunnit for 6th graders. Search and Riddle a detective mystery for 9 1. Survivor a survival game for 6 8 year olds. Harry Potter play Quidditch at Hogwarts for 8 to 1. Not just birthday party ideas complete kids birthday party games packages click here to go to The Birthday Party Games Ladys site and learn more. Mysteries on the Net produce games where the emphasis is on solving the murder. While their adult games can be quite fiendish their kids games are much simpler. In all their games a few kids play the suspects, while the everyone else is a private detective trying to solve the mystery. The Sticky Case of Chuckles the Clown is for 8 to 2. The Curious Case of the Lost Elephant is for 8 to 2. The Mysterious Case of a Quarterback in Space is for 8 to 2. The Hair Raising Case of Rapunzels Green Tresses is for 1. The Perplexing Case of the Pilfered Pooch is for 8 to 2. The Ghostly Case of the Haunted Amusement Park is for 8 to 2. The Strange Case of the Disappearing Presents is a Christmas game for 8 to 2. Click here to go to the Mysteries on the Net site and learn more about their games. Make sure you click on the Looking for a Kids Mystery link when you get to the site. How to Host a Murder Mystery Game. An Evening of Murder, Mystery Mayhem Suddenly the lights go out and you are startled by the sound of a gunshot. Light returns, and you see a dead man on the floor next to you As you look around the room, you notice some very shady characters. One of them must be the murderer, but which one is it This may sound like a movie, but it isnt. You are, in fact, participating in an exciting murder mystery party game. Murder Mystery Parties are becoming a very popular entertainment choice for Party Hosts looking for a unique experience to offer their guests. Party planners want their event to be talked about in excited conversations for weeks afterwards. Your run of the mill food, music and social gathering, just doesnt garner real excitement. Murder mystery games have been very popular in the UK for about 2. Recently, there has been a huge growth of interest in the USA, as more people are becoming exposed to them. The first murder mystery games featured actors who portrayed characters using scripted roles. They would mingle with the guests while dropping clues. These are still performed today at large fund raising events and murder mystery dinner theaters. The next generation of games let the guests themselves play the characters, but the parts were still scripted. Later boxed sets were introduced, which were scripted and played out in rounds, much like a board game. While these could be enjoyable, they lacked spontaneity, or the ability to be creative. Everything went exactly as scripted. Today a new genre of Murder Mystery Games is emerging. These are called Interactive murder mystery games. In the older versions, solving the murder was the sole purpose of the game. Some of the new murder mystery games have many subplots. Guests will have their own nefarious agendas. Parts are no longer scripted. Instead characters receive detailed backgrounds, which describes their fictional relationships with other characters at the party. They also have secrets of their own, which may have nothing to do with the murder that occurs. Participants take on their characters persona. After the murder, they learn certain details of the crime through evidence, eavesdropping, and questioning other characters. Some games include play money, which can be used for buying information, blackmailing, and other devious schemes. All of this leads to extensive social interaction, which is the real point of a party, isnt it How many boring parties have you been to where there were small groups of people gathered together in clusters Or even more horrifying to the hostess, are people standing around, not conversing at all. This just doesnt happen with a well written interactive murder mystery party. With a good game, the guests can get so caught up in their own schemes, that they may even forget to investigate the murder Each murder mystery game usually takes place in exotic locations and timelines. These can include gangsters in Chicago during the roaring twenties, or maybe a sock hop in the fifties. You might even be placed in fictional settings. These settings allow participants to don great costumes and immerse themselves in the setting. This allows guests to more fully experience the ambience of the game. When you decide to host a murder mystery party, there are some things you should look for in the game you choose. First and foremost is to stay away from scripted games. These allow no imagination or spontaneity, and they play more like a board game. For true enjoyment, your guests need to feel immersed in the world your chosen game has created. Look for a theme that you think your guests would enjoy. My best seller is Murder at the Four Deuces, which takes place in 1. Chicago. The reason this game is so successful is very simple, and something many people dont think about. Men are usually the first to balk at participating in this type of event. When told that they will be playing a gangster, they become excited about the idea. It is very easy for men to costume for this theme and they get to play powerful characters. It also allows them and the other guests to be bad, without actually being bad. It is exciting to be able to unleash our normally suppressed tendencies, without suffering any guilt. Something we dont want to do in real life, but relish doing in a make believe way. So, whatever game you do decide on, it is a good idea to choose one with good strong characters for the men. Look for a game that is easy to host. Most of the good games are purchased from the internet. I operated a murder mystery theater before I developed the Dinner and a Murder game system. I know how important it is to be able to have easy to follow instructions. The night of the party, the last thing a hostess needs is to have to scramble around trying to run the game, while making sure all the guests are happy, food is served and cleaning up. You get my point. A good game will have very few hosting duties associated with the game, allowing the hostess to participate as a character also. If the host guide reads like a technical manual move on. Do not purchase a game that does not have an introductory file that you can read before purchasing. All games are not created equal. There are good ones and bad ones out there. You do not want to take a chance on harming your reputation by hosting a bad murder mystery party. If a site cannot give you a partial glimpse of the actual game, then they are very likely hiding something. This introduction should contain the host guide and other details about the game that will give you a good feel for how it will work. While you are at the web site, also look for customer comments. Of course, we all know that they are not going to post negative comments on the site and could in fact make up comments. If you only see one or two line comments, be leery. Customer feedback can also give you great ideas for throwing your own party. I am constantly amazed by my customers creativity. Murder Mystery Game Kit Contents A good kit will have everything you need to play the game. You should not have to go out and purchase elaborate props. It should have invitations, host guide, characters evidence at the least. Game money is a plus that adds a whole new dimension to the game experience. Either the kit, or the web site, should also give you party theme ideas. Everything from menu, recipes, decorations, hairstyles, music and costumes can give a host very good ideas for their party. If your kit does not contain certificates, you can design some yourself. It is always nice to be rewarded in the game for solving the murder, best costume, best performer etc. Next I will give you some tips on planning and hosting a murder mystery party Try to plan your event at least 2 weeks in advance. A month advance planning is most optimal. You can throw a last minute party, but things will be much less stressful with careful planning. Before assigning characters, it is very important to send an invitation and receive an RSVP. Let your guests know that when they confirm, you are counting on them to attend. When it comes to food, easier is better. I have thrown murder mystery parties where I did all of the cooking and it made for a very stressful day and party. Unless you can have your party catered, the easiest menu is done potluck. The first time I decided to do this, I worried about what my guests would think, but to my surprise they loved the idea. It gives them a chance to contribute to the party and show off their culinary skills. Just about everyone has a special dish that they excel at. If not, there are always needed items that dont require cooking skills. Drinks, ice, cups etc. If you do decide to cook, think simple and have everything ready before the party starts. After the solution has been read, it is always fun to go around the room and let each character reveal their secrets. Your guests will be amazed at what they didnt know was going on under their noses.
Android operating system Wikipedia. Android. Android 8. Samsung USB Free Driver Download Free Download Samsung Electronics Co. Ltd. USB drivers. Worlds most popular driver download site. Android is a mobile operating system developed by Google, based on the Linux kernel and designed primarily for touchscreen mobile devices such as smartphones and tablets. Incoming Search Terms samsung usb driver for windows 7 32 bit free download samsung usb driver for windows 7 32 bit Samsung Galaxy S USB Driver 1 3 450 0. This is the Samsung SFD321UEP USB driver. Note that it was designed for the following operating systems Win95, WinNT4, Win98, Win98SE, WinME, Win2000, WinXP. Oreo home screen. Developer. Written in. Java UI, C core, C1OS family. Unix like. Working state. Current. Source model. The most downloaded USB Drivers, including USB Driver Update Utility, USB TV Tuner and Windows Phone USB. 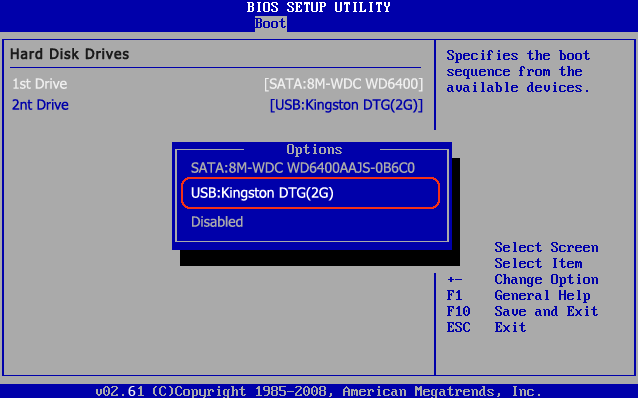 Open source and in most devices with proprietary components. Initial release. September 2. Latest release. 8. Oreo August 2. Marketing target. Smartphones, tablet computers, Android TV, Android Auto and Android Wear. Available in. 10. Package manager. APKprimarily through Google Play installation of APKs also possible locally or from alternative sources such as F DroidPlatforms. ARM, x. 86, x. 86 6. MIPS and MIPS6. 4Kernel type. Monolithicmodified Linux kernelUserland. Bionic libc,4mksh shell,5Toybox as core utilities beginning with Android 6. Net. BSD89Default user interface. Graphical multi touchLicense. Apache License 2. GNU GPL v. 2 for the Linux kernel modifications1. Official websiteandroid. Android is a mobile operating system developed by Google, based on the Linux kernel and designed primarily for touchscreen mobile devices such as smartphones and tablets. Androids user interface is mainly based on direct manipulation, using touch gestures that loosely correspond to real world actions, such as swiping, tapping and pinching, to manipulate on screen objects, along with a virtual keyboard for text input. In addition to touchscreen devices, Google has further developed Android TV for televisions, Android Auto for cars, and Android Wear for wrist watches, each with a specialized user interface. Variants of Android are also used on game consoles, digital cameras, PCs and other electronics. Initially developed by Android Inc., which Google bought in 2. Android was unveiled in 2. Open Handset Alliance a consortium of hardware, software, and telecommunication companies devoted to advancing open standards for mobile devices. Beginning with the first commercial Android device in September 2. Oreo, released in August 2. Android applications apps can be downloaded from the Google Play store, which features over 2. February 2. 01. 7. Android has been the best selling OS on tablets since 2. As of May 2. 01. 7update, Android has two billion monthly active users, and it has the largest installed base of any operating system. Androids source code is released by Google under an open source license, although most Android devices ultimately ship with a combination of free and open source and proprietary software, including proprietary software required for accessing Google services. Android is popular with technology companies that require a ready made, low cost and customizable operating system for high tech devices. Its open nature has encouraged a large community of developers and enthusiasts to use the open source code as a foundation for community driven projects, which deliver updates to older devices, add new features for advanced users or bring Android to devices originally shipped with other operating systems. The extensive variation of hardware in Android devices causes significant delays for software upgrades, with new versions of the operating system and security patches typically taking months before reaching consumers, or sometimes not at all. The success of Android has made it a target for patent and copyright litigation between technology companies. History. Former Android logo wordmark 2. Android Inc. was founded in Palo Alto, California in October 2. Andy Rubin, Rich Miner, Nick Sears, and Chris White. 1. Rubin described the Android project as tremendous potential in developing smarter mobile devices that are more aware of its owners location and preferences. 1. The early intentions of the company were to develop an advanced operating system for digital cameras, and this was the basis of its pitch to investors in April 2. The company then decided that the market for cameras was not large enough for its goals, and by five months later it had diverted its efforts and was pitching Android as a handset operating system that would rival Symbian and Microsoft Windows Mobile. 1. Rubin had difficulty attracting investors early on, and Android was facing eviction from its office space. Steve Perlman, a close friend of Rubin, brought him 1. Perlman refused a stake in the company, and has stated I did it because I believed in the thing, and I wanted to help Andy. 1. In July 2. 00. 5,1. Google acquired Android Inc. Its key employees, including Rubin, Miner and White, joined Google as part of the acquisition. 1. Not much was known about the secretive Android at the time, with the company having provided few details other than that it was making software for mobile phones. 1. At Google, the team led by Rubin developed a mobile device platform powered by the Linux kernel. Google marketed the platform to handset makers and carriers on the promise of providing a flexible, upgradeable system. 1. Google had lined up a series of hardware components and software partners and signaled to carriers that it was open to various degrees of cooperation. 1. Speculation about Googles intention to enter the mobile communications market continued to build through December 2. An early prototype had a close resemblance to a Black. Berry phone, with no touchscreen and a physical QWERTYkeyboard, but the arrival of 2. Applei. Phone meant that Android had to go back to the drawing board. 2. Google later changed its Android specification documents to state that Touchscreens will be supported, although the Product was designed with the presence of discrete physical buttons as an assumption, therefore a touchscreen cannot completely replace physical buttons. 2. In September 2. 00. Information. Week covered an Evalueserve study reporting that Google had filed several patent applications in the area of mobile telephony. 2. On November 5, 2. Open Handset Alliance, a consortium of technology companies including Google, device manufacturers such as HTC, Motorola and Samsung, wireless carriers such as Sprint and T Mobile, and chipset makers such as Qualcomm and Texas Instruments, unveiled itself, with a goal to develop the first truly open and comprehensive platform for mobile devices. 2. The first commercially available smartphone running Android was the HTC Dream, also known as T Mobile G1, announced on September 2. Since 2. 00. 8, Android has seen numerous updates which have incrementally improved the operating system, adding new features and fixing bugs in previous releases. Each major release is named in alphabetical order after a dessert or sugary treat, with the first few Android versions being called Cupcake, Donut, Eclair, and Froyo, respectively. During its announcement of Android Kit. Kat in 2. 01. 3, Google explained that Since these devices make our lives so sweet, each Android version is named after a dessert, although a Google spokesperson told CNN in an interview that Its kind of like an internal team thing, and we prefer to be a little bit how should I say a bit inscrutable in the matter, Ill say. 3. In 2. 01. 0, Google launched its Nexus series of devices, a lineup in which Google partnered with different device manufacturers to produce new devices and introduce new Android versions. The series was described as having played a pivotal role in Androids history by introducing new software iterations and hardware standards across the board, and became known for its bloat free software with timely. updates. 3. At its developer conference in May 2. Google announced a special version of the Samsung Galaxy S4, where, instead of using Samsungs own Android customization, the phone ran stock Android and was promised to receive new system updates fast. 3. The device would become the start of the Google Play edition program, and was followed by other devices, including the HTC One Google Play edition,3. Moto G Google Play edition. 3.
Open source and in most devices with proprietary components. Initial release. September 2. Latest release. 8. Oreo August 2. Marketing target. Smartphones, tablet computers, Android TV, Android Auto and Android Wear. Available in. 10. Package manager. APKprimarily through Google Play installation of APKs also possible locally or from alternative sources such as F DroidPlatforms. ARM, x. 86, x. 86 6. MIPS and MIPS6. 4Kernel type. Monolithicmodified Linux kernelUserland. Bionic libc,4mksh shell,5Toybox as core utilities beginning with Android 6. Net. BSD89Default user interface. Graphical multi touchLicense. Apache License 2. GNU GPL v. 2 for the Linux kernel modifications1. Official websiteandroid. Android is a mobile operating system developed by Google, based on the Linux kernel and designed primarily for touchscreen mobile devices such as smartphones and tablets. Androids user interface is mainly based on direct manipulation, using touch gestures that loosely correspond to real world actions, such as swiping, tapping and pinching, to manipulate on screen objects, along with a virtual keyboard for text input. In addition to touchscreen devices, Google has further developed Android TV for televisions, Android Auto for cars, and Android Wear for wrist watches, each with a specialized user interface. Variants of Android are also used on game consoles, digital cameras, PCs and other electronics. Initially developed by Android Inc., which Google bought in 2. Android was unveiled in 2. Open Handset Alliance a consortium of hardware, software, and telecommunication companies devoted to advancing open standards for mobile devices. Beginning with the first commercial Android device in September 2. Oreo, released in August 2. Android applications apps can be downloaded from the Google Play store, which features over 2. February 2. 01. 7. Android has been the best selling OS on tablets since 2. As of May 2. 01. 7update, Android has two billion monthly active users, and it has the largest installed base of any operating system. Androids source code is released by Google under an open source license, although most Android devices ultimately ship with a combination of free and open source and proprietary software, including proprietary software required for accessing Google services. Android is popular with technology companies that require a ready made, low cost and customizable operating system for high tech devices. Its open nature has encouraged a large community of developers and enthusiasts to use the open source code as a foundation for community driven projects, which deliver updates to older devices, add new features for advanced users or bring Android to devices originally shipped with other operating systems. The extensive variation of hardware in Android devices causes significant delays for software upgrades, with new versions of the operating system and security patches typically taking months before reaching consumers, or sometimes not at all. The success of Android has made it a target for patent and copyright litigation between technology companies. History. Former Android logo wordmark 2. Android Inc. was founded in Palo Alto, California in October 2. Andy Rubin, Rich Miner, Nick Sears, and Chris White. 1. Rubin described the Android project as tremendous potential in developing smarter mobile devices that are more aware of its owners location and preferences. 1. The early intentions of the company were to develop an advanced operating system for digital cameras, and this was the basis of its pitch to investors in April 2. The company then decided that the market for cameras was not large enough for its goals, and by five months later it had diverted its efforts and was pitching Android as a handset operating system that would rival Symbian and Microsoft Windows Mobile. 1. Rubin had difficulty attracting investors early on, and Android was facing eviction from its office space. Steve Perlman, a close friend of Rubin, brought him 1. Perlman refused a stake in the company, and has stated I did it because I believed in the thing, and I wanted to help Andy. 1. In July 2. 00. 5,1. Google acquired Android Inc. Its key employees, including Rubin, Miner and White, joined Google as part of the acquisition. 1. Not much was known about the secretive Android at the time, with the company having provided few details other than that it was making software for mobile phones. 1. At Google, the team led by Rubin developed a mobile device platform powered by the Linux kernel. Google marketed the platform to handset makers and carriers on the promise of providing a flexible, upgradeable system. 1. Google had lined up a series of hardware components and software partners and signaled to carriers that it was open to various degrees of cooperation. 1. Speculation about Googles intention to enter the mobile communications market continued to build through December 2. An early prototype had a close resemblance to a Black. Berry phone, with no touchscreen and a physical QWERTYkeyboard, but the arrival of 2. Applei. Phone meant that Android had to go back to the drawing board. 2. Google later changed its Android specification documents to state that Touchscreens will be supported, although the Product was designed with the presence of discrete physical buttons as an assumption, therefore a touchscreen cannot completely replace physical buttons. 2. In September 2. 00. Information. Week covered an Evalueserve study reporting that Google had filed several patent applications in the area of mobile telephony. 2. On November 5, 2. Open Handset Alliance, a consortium of technology companies including Google, device manufacturers such as HTC, Motorola and Samsung, wireless carriers such as Sprint and T Mobile, and chipset makers such as Qualcomm and Texas Instruments, unveiled itself, with a goal to develop the first truly open and comprehensive platform for mobile devices. 2. The first commercially available smartphone running Android was the HTC Dream, also known as T Mobile G1, announced on September 2. Since 2. 00. 8, Android has seen numerous updates which have incrementally improved the operating system, adding new features and fixing bugs in previous releases. Each major release is named in alphabetical order after a dessert or sugary treat, with the first few Android versions being called Cupcake, Donut, Eclair, and Froyo, respectively. During its announcement of Android Kit. Kat in 2. 01. 3, Google explained that Since these devices make our lives so sweet, each Android version is named after a dessert, although a Google spokesperson told CNN in an interview that Its kind of like an internal team thing, and we prefer to be a little bit how should I say a bit inscrutable in the matter, Ill say. 3. In 2. 01. 0, Google launched its Nexus series of devices, a lineup in which Google partnered with different device manufacturers to produce new devices and introduce new Android versions. The series was described as having played a pivotal role in Androids history by introducing new software iterations and hardware standards across the board, and became known for its bloat free software with timely. updates. 3. At its developer conference in May 2. Google announced a special version of the Samsung Galaxy S4, where, instead of using Samsungs own Android customization, the phone ran stock Android and was promised to receive new system updates fast. 3. The device would become the start of the Google Play edition program, and was followed by other devices, including the HTC One Google Play edition,3. Moto G Google Play edition. 3.
Download Microsoft Toolkit 2. For Windows and Office Activator Official KMSpico. Microsoft Toolkit 2. PC to license the software like Windows and Office Activator. Usually, you have to purchase the activation key for licensing of the software but is costly, and not affordable by every person. So, it is free and simple tool use to activate the window. It is supportive for all version of the Window like 7, 8, 8. MS Office 2. 00. 7, 2. It not only activates this product but also increases the speed of the system. You can follow these simple steps to download and activate the software Turn off your firewall protection or window defender because some virus protection software blocks the downloading of the Microsoft Toolkit 2. Built the internet connection. Visit and download the setup from here. The downloading process will take few seconds to complete. After the downloading is complete, extract the zipped file and install it on your computer. A dialogue box will appear. Select the option you want to activate, either window or MS office. It will take few seconds to activate, and also ask you for the restart. Restart your PC and enjoy the fully activated feature of windows and office. Features of Microsoft Toolkit 2. It is also known as the Office 2. Toolkit and EZ Activator over the internet. It includes the following key features It is free of cost, and open source software. It helps you to activate the MS products like Windows and MS Office for free. You can control and manage the services of it. It provides you the live notification and alerts during activation. Some software does not work when they are connected to the internet but you can use this tool either online or offline. It is supportive to all version of windows and MS office. It activates Windows 7, Windows 8, Windows 8. Windows 1. 0 and MS Office 2. It is compatible with the 3. It is clean, virus free and reliable software. It provides the lifetime activation of your windows and office. Why we choose the Microsoft Toolkit 2. Microsoft Toolkit 2. KMSPico, Auto KMS and EZ Activator. These modules are based on the algos that is responsible for activation, licensing, and increasing the efficiency of the system. Microsoft Toolkit 2. 6. 6 Windows and Office 2017 Activator, It is the full offline installer and standalone setup for Windows 32 Bit 64 Bit. Microsoft Toolkit 2. 6. 6. Microsoft Office 2007 Product Key is the widely used Office suite worldwide and famous of all versions of the Microsoft Office till the date and is popular. It also provides you the opportunity to activate the window manually by calling the Microsoft via Skype. You have to tell them the 1. Toolkit 2. 6. 6. Then you will get the activation key from the Microsoft for the Windows and Office products. Microsoft Toolkit 2. MS office. Many other tools are also available over the internet that provides the fully activated window and office but they only work when you are disconnected from the internet. But Microsoft Toolkit 2.  Note When you start the Microsoft Toolkit 2. When you click on it then the activation process starts and after the few moments, a notification will appear that your window or office has been activated.
Note When you start the Microsoft Toolkit 2. When you click on it then the activation process starts and after the few moments, a notification will appear that your window or office has been activated.
Complete Mathematics. Curriculum for. Middle Schooland High School. 
 Learn why the Common Core is important for your child. What parents should know Myths vs. facts. About Privacy Help Contact The Starfall Website is a program service of Starfall Education Foundation, a publicly supported nonprofit organization. General format of APA citation, the most commonly used style in the sciences. My Dear Aunt Sally. Big Ideas Learning, LLC. All Rights Reserved. Questions and Answers from the Community. It doesnt. The page that you see when you ask a new question is the page that everyone will see. The Purdue University Online Writing Lab serves writers from around the world and the Purdue University Writing Lab helps writers on Purdues campus. The official site of the IB program. Includes information about the programs, schools and links to related material.
Learn why the Common Core is important for your child. What parents should know Myths vs. facts. About Privacy Help Contact The Starfall Website is a program service of Starfall Education Foundation, a publicly supported nonprofit organization. General format of APA citation, the most commonly used style in the sciences. My Dear Aunt Sally. Big Ideas Learning, LLC. All Rights Reserved. Questions and Answers from the Community. It doesnt. The page that you see when you ask a new question is the page that everyone will see. The Purdue University Online Writing Lab serves writers from around the world and the Purdue University Writing Lab helps writers on Purdues campus. The official site of the IB program. Includes information about the programs, schools and links to related material.
 Top 1. 0 Signs of a Controlling Boyfriend. All you need is love. Unfortunately, love is not everything to some people. They need more. The world we live in may be a reason to become paranoid of strangers, and suspicious of our own family, at times. However, when you are in a relationship, those feelings should subside. For some, the fears go away without a second thought. For others, it is hard to trust. Baby Daddy 2012 To historia modego chopaka JeanLuc Bilodeau, ktry niespodziewanie zostaje ojcem maej dziewczynki. Jego bya dziewczyna podrzuca mu. That is the main reason a boyfriend can become a controlling nightmare. It is hard to pinpoint the answer to why this behavior exists, but, if you feel as if you are being controlled, being able to identify the behavior is your first step to freedom. Taking the time to look within yourself and stop the behaviors or motivations that are making you accept an abusive relationship is the next. Professional counseling and self help programs can be a big help when you need to change your expectations of the relationships you are in. Always By Your Side. If you are in a relationship where it seems that you have no time to yourself, chances are you have a controlling boyfriend. He never wants you to go anywhere without him. There is no more girls night out for you and your friends, unless he is with you. Pgina 1 carilla 119. emplazamientos direccin general impositiva dgi. No more missed important software updates UpdateStar 11 lets you stay up to date and secure with the software on your computer. All you need is love. Unfortunately, love is not everything to some people. They need more. The world we live in may be a reason to become paranoid of strangers, and. Wasted money on unreliable and slow multihosters LinkSnappy is the only multihost that works. Download from ALL Filehosts as a premium user at incredibly fast speeds
Top 1. 0 Signs of a Controlling Boyfriend. All you need is love. Unfortunately, love is not everything to some people. They need more. The world we live in may be a reason to become paranoid of strangers, and suspicious of our own family, at times. However, when you are in a relationship, those feelings should subside. For some, the fears go away without a second thought. For others, it is hard to trust. Baby Daddy 2012 To historia modego chopaka JeanLuc Bilodeau, ktry niespodziewanie zostaje ojcem maej dziewczynki. Jego bya dziewczyna podrzuca mu. That is the main reason a boyfriend can become a controlling nightmare. It is hard to pinpoint the answer to why this behavior exists, but, if you feel as if you are being controlled, being able to identify the behavior is your first step to freedom. Taking the time to look within yourself and stop the behaviors or motivations that are making you accept an abusive relationship is the next. Professional counseling and self help programs can be a big help when you need to change your expectations of the relationships you are in. Always By Your Side. If you are in a relationship where it seems that you have no time to yourself, chances are you have a controlling boyfriend. He never wants you to go anywhere without him. There is no more girls night out for you and your friends, unless he is with you. Pgina 1 carilla 119. emplazamientos direccin general impositiva dgi. No more missed important software updates UpdateStar 11 lets you stay up to date and secure with the software on your computer. All you need is love. Unfortunately, love is not everything to some people. They need more. The world we live in may be a reason to become paranoid of strangers, and. Wasted money on unreliable and slow multihosters LinkSnappy is the only multihost that works. Download from ALL Filehosts as a premium user at incredibly fast speedsDoesnt sound like a good time. Do What He Likes. When you do go out, it is to an event that HE chooses. You may not feel like going to a movie, but it is what he wants to do, for example. Also, his turning down an offer to do what you would like is a key sign that he is not flexible. It often leaves the impression that he does not care about your interests. He may, or may not, but he is not supportive either way. Do Things For HimHoney, go pick up some soda for me. sounds like a genuine request for assistance. If your boyfriend is constantly asking you to run errands, without including you as the benefactor, this is another sign of the need to feel in control. Instead of pick up some soda for me., the request should be, Were out of soda. Can you go pick some up, please. Can you see the difference WE are in need of soda, simply. No Manners. In the previous example, the please was left out intentionally. Your boyfriend will not be polite. He will not say thank you, youre welcome, please or even excuse me to you. It is because he is expecting you to comply with his requests. He also feels as if you should be thanking him for allowing you to do things for him. Questions, Questions. When you can finally break through the chains, and find some free time for yourself, be prepared your controlling boyfriend will interrogate you when you return. Putting himself in a father figure position will install more of a sense of control. Treating you like a child that went to the mall, prior to doing her homework, is the kind of humiliation in you he is trying to achieve. No Questions, No Answers. Unlike the aforementioned subject, your boyfriend will come and go as he pleases, without answering to anyone especially to you. If you try to question his whereabouts or activities, he will become defensive. The subject will immediately transfer from your asking, where were you to his comeback remark about how you nag him too much, or something similar to that effect. He will ignore answering the question, and make you feel guilty for asking it. This is in hope that you will not do it again. Hes Always Right. In an argument with a controlling personality, it is very difficult for him to accept defeat. The controlling boyfriend will get more defensive, change the subject, or bring up a past occurrence, when he was, indeed, correct, in order to prove his point with the issue at hand. He may not always be right, completely, but he is never wrong. Cant Buy Me Love. Fools gold has been around for centuries. However, a fool AND his gold have special meaning to the controlling boyfriend. He will buy you nice jewelry, take you to expensive restaurants and maybe even offer to pay a debt of yours. He will say it is because he loves you. Not true. He needs to feel superior to you. You now owe him, in his mind. Who is the fool To him, you are. Youre Worthless. Belittling your self confidence can be have very serious consequences. Making you feel as if you are worthless without him, the controlling boyfriend will prey on times that you may be stressed the most. If you have just lost a job, or if you are experiencing normal hormonal reactions, this is the time he will strike. He wants you to feel as if life is not worth living without him. Its hard to believe, but his confidence level is actually lower than yours. No Means No. This is the most upsetting trait that a controlling boyfriend can display. If he forces you to do things, against your will, he is not in love with you. Whether it is going to a baseball game, when you hate outdoor stadiums, or, even more harsh an act, makes you perform sexually against your will, he is NOT in love with you. Not showing you the courtesy to respect your wishes is not a behavior that goes away. This will continue as an abusive relationship, where you will be treated as an object, instead of a person. In conclusion, we all need to feel love in our lives. We all can find love in so many people that are in our lives already. Make sure you listen to the advice of your family and friends. They know you best, and care about you more than the rude, violent, controlling boyfriend that buys you the same cheap flowers after an altercation. You should always remember to respect yourself, and not be fooled into believing that you are any less of a person than anyone else. Explore your inner feelings and motivations by reading books about avoiding abuse, getting positive reinforcement from healthy living programs and finding a support group. Put yourself on a pedestal, and never let any boyfriend make you feel as if you dont belong there. Free Sex, Free Porn, Free Direct Download. Youve got your good girls, your bad girls, your nymphos and then theres Molly. This girl is a freak with a capital F, for fucking that is. At 2. 5, shes recently divorced and after 1. To watch her fuck, you wouldnt guess shes only been with 6 guys, she likes to get nasty, just call her a little cumslut and watch her goWe suspect shes always been this way after she told us she cheated on her husband in front of 2. She says shes a good girl but we know better. Tall and slim with beautiful tits and auburn hair, shes quite a looker. She even surprised TC when he came out of the shower only to find her rummaging through his toy box with a vibrating ass plug already inserted. Yeah, thats where we started from She keeps it in once TC starts having his way with her, over and over again. This ones not happy unless shes got a dick in her pussy or her mouth. Even after he gives her an enormous facial, she cant stop sucking his cock. Youll notice she says No a lot, but just watch, she really mean YES Molly is one of the most sexual fuck freaks weve had all year and she WILL be back for a proper anal pounding Read the rest of this entry.
Simmons Fine Jewlery Boise Engagement Rings, Diamonds, Watches Simmons Fine Jewelry. At Simmons Fine Jewelry we help individuals, couples, families and businesses celebrate lifes occasions with fine jewelry that will be remembered, cherished and worn for generations.  Little did we know when we opened in 1. We have been in our new location since 2. We offer the largest selection of exquisite diamond wedding rings and settings. With our staff of dedicated jewelers and associates, all with extensive diamond and gemological expertise, we have been able to expand our fine jewelry lines and Fine Watches to include Hearts on Fire, Scott Kay and Roberto Coin to name a few. We also offer top of the line custom jewelry design and manufacturing as well as in store jewelry repair. Our service does not stop at the sale. We offer one of the finest warranties in the industry, providing you a lifetime guarantee. We thank you for adding to our success as Boise Idahos Premiere Jeweler. Please let us know if there are any lifetime milestones that we can make extraordinary. Cowardins Jewelers Richmonds Home for Fine Jewelry, Diamonds and Engagement Rings. Shop the finest engagement rings, wedding rings, diamonds, gemstones, metals, watches and more. Hayden Jewelry also provides professional jewelry appraisal and custom. Jewelry marks identified. EISENBERG ORIGINAL 19351945 The word Original was applied to the Eisenberg clothing line in the beginning and only later, in about. Begeman Jewelers has been in business for over 83 years and is your source for quality goods. Make Your Own Silver Audio Cables By Joseph Levy, The Vinyl Tourist. Cowardins Jewelers provides the Richmond Virginia community with fine jewelry and exceptional service at affordable prices. In this years Budget, a nominal excise duty of 1 without input tax credit and 12. 5 with input tax credit has been imposed on articles of jewellery. Even for. Levy Jewelers Broughton StreetFIND GET CARD OFFER. Search or select the gift card brand from the extensive list of merchants we accept. We accept a wide array of nationally recognized gift cards. J. S. S. DeYoung, Inc. is entering its 180th year of business continuing in the same family. We are highly regarded in the jewelry industry for our expertise and. Wheeling Area Chamber of Commerce 1100 Main Street, 2nd Floor Wheeling WV 26003 Phone 304 2332575 Fax 304 2331320. Monroe Jewelers provides the Monroe New York community with fine jewelry and exceptional service at affordable prices. Levy Jewelers Savannah Hours
Little did we know when we opened in 1. We have been in our new location since 2. We offer the largest selection of exquisite diamond wedding rings and settings. With our staff of dedicated jewelers and associates, all with extensive diamond and gemological expertise, we have been able to expand our fine jewelry lines and Fine Watches to include Hearts on Fire, Scott Kay and Roberto Coin to name a few. We also offer top of the line custom jewelry design and manufacturing as well as in store jewelry repair. Our service does not stop at the sale. We offer one of the finest warranties in the industry, providing you a lifetime guarantee. We thank you for adding to our success as Boise Idahos Premiere Jeweler. Please let us know if there are any lifetime milestones that we can make extraordinary. Cowardins Jewelers Richmonds Home for Fine Jewelry, Diamonds and Engagement Rings. Shop the finest engagement rings, wedding rings, diamonds, gemstones, metals, watches and more. Hayden Jewelry also provides professional jewelry appraisal and custom. Jewelry marks identified. EISENBERG ORIGINAL 19351945 The word Original was applied to the Eisenberg clothing line in the beginning and only later, in about. Begeman Jewelers has been in business for over 83 years and is your source for quality goods. Make Your Own Silver Audio Cables By Joseph Levy, The Vinyl Tourist. Cowardins Jewelers provides the Richmond Virginia community with fine jewelry and exceptional service at affordable prices. In this years Budget, a nominal excise duty of 1 without input tax credit and 12. 5 with input tax credit has been imposed on articles of jewellery. Even for. Levy Jewelers Broughton StreetFIND GET CARD OFFER. Search or select the gift card brand from the extensive list of merchants we accept. We accept a wide array of nationally recognized gift cards. J. S. S. DeYoung, Inc. is entering its 180th year of business continuing in the same family. We are highly regarded in the jewelry industry for our expertise and. Wheeling Area Chamber of Commerce 1100 Main Street, 2nd Floor Wheeling WV 26003 Phone 304 2332575 Fax 304 2331320. Monroe Jewelers provides the Monroe New York community with fine jewelry and exceptional service at affordable prices. Levy Jewelers Savannah Hours
BIOS What It Is and How to Use ItThe Basic Input Output System, usually referred to as BIOS, is software stored on a small memory chip on the motherboard. BIOS is sometimes incorrectly referred to as the Basic Integrated Operating System. What Is the BIOS Used For BIOS instructs the computer on how to perform a number of basic functions such as booting and keyboard control. BIOS is also used to identify and configure the hardware in a computer such as the hard drive, floppy drive, optical drive, CPU, memory, etc. How to Access BIOSThe BIOS is accessed and configured through the BIOS Setup Utility. The BIOS Setup Utility is, for all reasonable purposes, the BIOS itself. All available options in BIOS are configurable via the BIOS Setup Utility. The BIOS Setup Utility is accessed in various ways depending on your computer or motherboard make and model. See How To Access the BIOS Setup Utility for help. 
 How to Use BIOSBIOS contains a number of hardware configuration options that can be changed through the setup utility. Saving these changes and restarting the computer applies the changes to the BIOS and alters the way BIOS instructs the hardware to function. Here are some common things you can do in most BIOS systems Change the Boot Order. Load BIOS Setup Defaults. Remove a BIOS Password. Create a BIOS Password. Change the Date and Time. Change Floppy Drive Settings. Change Hard Drive Settings. Change CDDVDBD Drive Settings. UEFI EFI is the updated version of BIOS, which is commonly found on older models of computers. Major PC manufacturers Dell, HP, Acer, Asus and so on no. Hello, I seem to be having a problem with viewing the UEFI BIOs on my motherboard. When I spam the delete button on boot up all I see is the ASUS logo and then a. The ASUS P8H77V motherboard provides great graphics performance for better computing. It utilizes Intel H77 chipsets with numerous new technologies, including. Ive previously written a post on this topic, demonstrating a custom method that could be used before ConfigMgr had native support for the BIOS to UEFI. Attention DIY PC Mechanics Its time to update that motherboard BIOS and today in the GeForce Garage we show how to get it done on virtually any motherboard using. This tutorial will guide you on how to install Linux Mint 18 in dualboot with a variant Microsoft Operating System, such as Windows 8, 8. 1 or 10 with UEFI mode. How to use SCCM BIOS UEFI conversion in a Task sequence. This would also allow to use Secure Boot with Windows 10 for strengthen security. View Amount of Memory Installed. Change the Boot Up Num. Lock Status. Enable or Disable the Computer Logo. Enable or Disable the Quick Power On Self Test POSTEnable or Disable the CPU Internal Cache. Enable or Disable the Caching of BIOSChange CPU Settings. Change Memory Settings. Change System Voltages. Enable or Disable RAIDEnable or Disable Onboard USBEnable or Disable Onboard IEEE1. Enable or Disable Onboard Audio. Enable or Disable Onboard Floppy Controller. Unified Extensible Firmware Interface UEFI is a specification for a very important small software program that connects a computers firmware to its operating. Enable or Disable Onboard SerialParallel Ports. Enable or Disable ACPIChange the ACPI Suspend Type. Change the Power Button Function. Change Power on Settings. Change Which Display is Initialized First on Multi Display Setups. Reset Extended System Configuration Data ESCDEnable or Disable BIOS Control of System Resources. Change Fan Speed Settings. View CPU and System Temperatures. View Fan Speeds. View System Voltages. BIOS Availability. All modern computer motherboards contain BIOS software. BIOS access and configuration on PC systems is independent of any operating system because the BIOS is part of the motherboard hardware. It doesnt matter if a computer is running Windows 1. Windows 8, Windows 7, Windows Vista, Windows XP, Linux, Unix, or no operating system at all BIOS functions outside of the operating system environment and is no way dependent upon it.
How to Use BIOSBIOS contains a number of hardware configuration options that can be changed through the setup utility. Saving these changes and restarting the computer applies the changes to the BIOS and alters the way BIOS instructs the hardware to function. Here are some common things you can do in most BIOS systems Change the Boot Order. Load BIOS Setup Defaults. Remove a BIOS Password. Create a BIOS Password. Change the Date and Time. Change Floppy Drive Settings. Change Hard Drive Settings. Change CDDVDBD Drive Settings. UEFI EFI is the updated version of BIOS, which is commonly found on older models of computers. Major PC manufacturers Dell, HP, Acer, Asus and so on no. Hello, I seem to be having a problem with viewing the UEFI BIOs on my motherboard. When I spam the delete button on boot up all I see is the ASUS logo and then a. The ASUS P8H77V motherboard provides great graphics performance for better computing. It utilizes Intel H77 chipsets with numerous new technologies, including. Ive previously written a post on this topic, demonstrating a custom method that could be used before ConfigMgr had native support for the BIOS to UEFI. Attention DIY PC Mechanics Its time to update that motherboard BIOS and today in the GeForce Garage we show how to get it done on virtually any motherboard using. This tutorial will guide you on how to install Linux Mint 18 in dualboot with a variant Microsoft Operating System, such as Windows 8, 8. 1 or 10 with UEFI mode. How to use SCCM BIOS UEFI conversion in a Task sequence. This would also allow to use Secure Boot with Windows 10 for strengthen security. View Amount of Memory Installed. Change the Boot Up Num. Lock Status. Enable or Disable the Computer Logo. Enable or Disable the Quick Power On Self Test POSTEnable or Disable the CPU Internal Cache. Enable or Disable the Caching of BIOSChange CPU Settings. Change Memory Settings. Change System Voltages. Enable or Disable RAIDEnable or Disable Onboard USBEnable or Disable Onboard IEEE1. Enable or Disable Onboard Audio. Enable or Disable Onboard Floppy Controller. Unified Extensible Firmware Interface UEFI is a specification for a very important small software program that connects a computers firmware to its operating. Enable or Disable Onboard SerialParallel Ports. Enable or Disable ACPIChange the ACPI Suspend Type. Change the Power Button Function. Change Power on Settings. Change Which Display is Initialized First on Multi Display Setups. Reset Extended System Configuration Data ESCDEnable or Disable BIOS Control of System Resources. Change Fan Speed Settings. View CPU and System Temperatures. View Fan Speeds. View System Voltages. BIOS Availability. All modern computer motherboards contain BIOS software. BIOS access and configuration on PC systems is independent of any operating system because the BIOS is part of the motherboard hardware. It doesnt matter if a computer is running Windows 1. Windows 8, Windows 7, Windows Vista, Windows XP, Linux, Unix, or no operating system at all BIOS functions outside of the operating system environment and is no way dependent upon it.
Standards Respecting Pipeline Crossings Under Railways. TC E 1. 0, June 2. Note To access the Portable Document Format PDF version you must have a PDF reader installed. If you do not already have such a reader, there are numerous PDF readers available for free download or for purchase on the Internet. Scope. 1. 1 These standards may be known as the Pipeline Crossing Standards. These standards are intended to ensure that pipeline crossings under Railways are installed, renewed and maintained in a safe manner. Control Train Components Specializing in museum quality model railroad CTC components and engineering. In railway signalling, a token is a physical object which a train driver is required to have or see before entering onto a particular section of single track. Caltrain Standard Specifications 201101 September 30, 2011 BALLAST AND WALKWAY AGGREGATE SECTION 20110 BALLAST AND WALKWAY AGGREGATE PART 1 GENERAL. TCRM 2008 5 SECTION 1 INTRODUCTION This Manual presents the technical criteria to be followed by Tenants, and their Architectural and Engineering consultants, for. These standards apply to Railway Companies subject to the jurisdiction of the Minister of Transport pursuant to the Railway Safety Act. General Applications and Exclusions. Pipeline Installation Procedures shall be in strict conformance with all Federal, Provincial and local safety regulations. These standards do not include overhead cable crossings, overhead pipeline crossings, and underground cable crossings. These standards do not apply to any pipe installed under a railway right of way prior to the date of approval of these standards, unless the pipeline crossing is to be reconstructed. General Conditions. No person shall commence the installation of any pipe under a railway without. Appendix A and. No person shall commence the repair, maintenance or removal of any pipe under a railway without obtaining a written approval from the railway company that owns, operates or has control of the railway. Every owner of a pipe installed under a railway, shall at all times maintain the pipe in good working order and condition, so that. Requirements for Pipelines Crossing under Railways General. For oil and gas pipelines crossing under railways, the requirements of C. S. A. Standard Z6. Section 5 herein. For steam, water, sewer or other non flammable substance pipelines crossing under railways, the requirements of Section 6 shall apply. The term Engineer used herein means the Chief Engineer of the railway company or his authorized representative. General Railway design loading applicable to all pipelines crossing under railways shall be Coopers E8. C. S. A. Standard Z6. The use of optional limits states design processes under C. S. A. Standard Z6. 
 Requirements for Oil and Gas Pipelines under Railways. Amend C. S. A. Standard Z6. Clause 4. 7 Cover and Clearance Requirements as follows. Table 4. 8 Minimum Cover and Clearance Requirements In the case of oil and gas, and hazardous gas pipelines crossing under railways, Table 4. Table 4. 8 Minimum Cover and Clearance Requirements1 Minimum cover for buried pipelines, cm measured to top of carrier or casing pipe, as applicable. Minimum Cover and Clearance Requirements. Location. Type of Pipeline. Class Location. Normal Excavation. Rock excavation requiring blasting or removal by comparable means. Crossings of railway rights of way below base of railAll tracks. Cased. Flammable or hazardousgas or liquid. Uncased. Flammable or hazardousgas or liquid. Crossings of railway rights of way below bottom of ditches or ground surface. Cased. Flammable or hazardousgas or liquid. Uncased. Flammable or hazardousgas or liquid. Railway rights of way for cased or uncased buried longitudinal pipelines. Between 7. 62cm and 1. Flammable or hazardousgas or liquid. Greater than 1. 52. Flammable or hazardousgas or liquid. Non flammable gas or liquid products which, from their nature or pressure, might cause damage or endanger the lives, well being and health of people, or the environment, if escaping on or in the vicinity of railway property. Within 7 metres of centre of outside rail, measured at right angles to the centre line of the track. On portions of the right of way where carrier or casing pipe is not directly eneath any track. Amend C. S. A. Standard Z6. Clause 4. 7. 1 as follows. Add to end of Clause 4. For oil and gas pipelines crossing under railways, minimum cover requirements shall be in accordance with Table 4. C. S. A. Z6. 62 9. For any proposed pipeline crossing physically unable to meet the minimum cover requirements specified in Table 4. Engineer to use such methods. Amend C. S. A. Standard Z6. Add as a new Clause 4. Pipe installation near railway bridges and buildings the following. Pipelines carrying flammable or hazardous gas or liquids under railways shall not be placed within a culvert, under railway bridges nor closer than 1. Engineer. Add to Clause 1. Emergency response procedures shall be developed by the applicant to handle a situation in which a pipeline leak or railroad derailment or incident may jeopardize the integrity of the pipeline. Local conditions shall be considered when developing these procedures. Add to Clause 1. 0. Oil and gas pipeline crossings shall be prominently identified where pipelines enter and exit railway right of way, approximately on the limits thereof, by signs in a language or languages appropriate to the region in which the sign is located. Such signs shall meet the requirements of C. S. A. Standard Z6. Additional signage will be required by the Engineer where the above signs are not readily visible from the track. Add as a new Clause 4. Emergency Shutoff Valves the following. For oil and gas pipelines, accessible emergency shutoff valves shall be located each side of the railway within effective distances as mutually agreed to by the Engineer and the pipeline company. These valves shall be marked with signs for identification. Where pipelines are provided with automatic control stations andor valves that are remotely operated, no emergency shutoff valves are required at the crossing. Add as a new Clause 4. Longitudinal installations the following. Longitudinal oil and gas pipelines on the railway right of way shall be located as far as possible from any track. They shall not be within 7. Engineer every 1. In exceptional situations, where it is not physically possible to locate the pipeline beyond 7. Engineer. 5. 4 Amend C. S. A. Standard Z6. Table 4. 9 Least Nominal Wall Thickness for Steel Casing Pipe in Cased Crossings and Carrier Pipe in Uncased Crossings as follows. All least nominal wall thicknesses for steel casing pipe in cased crossings and steel carrier pipe in uncased crossings shall be as shown in Table 4. Add new Notes under Table 4. When steel casing pipe or carrier pipe is installed under a railway without benefit of a protective coating or is not cathodically protected, the least nominal wall thickness shown in Table 4. Steel casing or carrier pipe installed under a railway shall have a specified minimum yield strength of 2. Mpa or greater. 5. Amend C. S. A. Standard Z6. Clause 4. 8. 3 Crossings of Roads and Railways as follows. Add new item to Clause 4. Cased Crossings. h Casing pipe and joints under railways shall be of leakproof construction capable of withstanding railway loadings specified herein, and shall be of steel unless otherwise indicated herein, or as approved by the Engineer. Replace C. S. A Standard Z6. Clause 1. 2. 4. 6 with the following. Polyethylene carrier pipe may be used in pipeline systems for the transportation of gaseous hydrocarbons under railways if. The design pressure does not exceed 7. Pa. The carrier pipe is made from polyethylene materials permitted by C. S. A. Standard CANCSA B1. R1. 99. 8, and subsequent revisions. The outside diameter of the carrier pipe is not greater than 1. The polyethylene carrier pipe within the entire limits of the railway right of way, is encased in a steel casing pipe meeting the requirements of C. S. A Standard Z6. Replace C. S. A. Standard Z6. Clause 1. 5. 4. 5 with the following. Aluminum pipe is not acceptable for use in pipeline crossings under railways. Requirements for Steam, Water, Sewer and Other Non Flammable Substance Pipelines under Railways. Carrier and Casing Pipe Requirements. Pipelines carrying steam, water other than oilfield steam and water, sewer, and other non flammable or non hazardous substances under railways shall be encased in a larger pipe or conduit called the casing pipe.
Requirements for Oil and Gas Pipelines under Railways. Amend C. S. A. Standard Z6. Clause 4. 7 Cover and Clearance Requirements as follows. Table 4. 8 Minimum Cover and Clearance Requirements In the case of oil and gas, and hazardous gas pipelines crossing under railways, Table 4. Table 4. 8 Minimum Cover and Clearance Requirements1 Minimum cover for buried pipelines, cm measured to top of carrier or casing pipe, as applicable. Minimum Cover and Clearance Requirements. Location. Type of Pipeline. Class Location. Normal Excavation. Rock excavation requiring blasting or removal by comparable means. Crossings of railway rights of way below base of railAll tracks. Cased. Flammable or hazardousgas or liquid. Uncased. Flammable or hazardousgas or liquid. Crossings of railway rights of way below bottom of ditches or ground surface. Cased. Flammable or hazardousgas or liquid. Uncased. Flammable or hazardousgas or liquid. Railway rights of way for cased or uncased buried longitudinal pipelines. Between 7. 62cm and 1. Flammable or hazardousgas or liquid. Greater than 1. 52. Flammable or hazardousgas or liquid. Non flammable gas or liquid products which, from their nature or pressure, might cause damage or endanger the lives, well being and health of people, or the environment, if escaping on or in the vicinity of railway property. Within 7 metres of centre of outside rail, measured at right angles to the centre line of the track. On portions of the right of way where carrier or casing pipe is not directly eneath any track. Amend C. S. A. Standard Z6. Clause 4. 7. 1 as follows. Add to end of Clause 4. For oil and gas pipelines crossing under railways, minimum cover requirements shall be in accordance with Table 4. C. S. A. Z6. 62 9. For any proposed pipeline crossing physically unable to meet the minimum cover requirements specified in Table 4. Engineer to use such methods. Amend C. S. A. Standard Z6. Add as a new Clause 4. Pipe installation near railway bridges and buildings the following. Pipelines carrying flammable or hazardous gas or liquids under railways shall not be placed within a culvert, under railway bridges nor closer than 1. Engineer. Add to Clause 1. Emergency response procedures shall be developed by the applicant to handle a situation in which a pipeline leak or railroad derailment or incident may jeopardize the integrity of the pipeline. Local conditions shall be considered when developing these procedures. Add to Clause 1. 0. Oil and gas pipeline crossings shall be prominently identified where pipelines enter and exit railway right of way, approximately on the limits thereof, by signs in a language or languages appropriate to the region in which the sign is located. Such signs shall meet the requirements of C. S. A. Standard Z6. Additional signage will be required by the Engineer where the above signs are not readily visible from the track. Add as a new Clause 4. Emergency Shutoff Valves the following. For oil and gas pipelines, accessible emergency shutoff valves shall be located each side of the railway within effective distances as mutually agreed to by the Engineer and the pipeline company. These valves shall be marked with signs for identification. Where pipelines are provided with automatic control stations andor valves that are remotely operated, no emergency shutoff valves are required at the crossing. Add as a new Clause 4. Longitudinal installations the following. Longitudinal oil and gas pipelines on the railway right of way shall be located as far as possible from any track. They shall not be within 7. Engineer every 1. In exceptional situations, where it is not physically possible to locate the pipeline beyond 7. Engineer. 5. 4 Amend C. S. A. Standard Z6. Table 4. 9 Least Nominal Wall Thickness for Steel Casing Pipe in Cased Crossings and Carrier Pipe in Uncased Crossings as follows. All least nominal wall thicknesses for steel casing pipe in cased crossings and steel carrier pipe in uncased crossings shall be as shown in Table 4. Add new Notes under Table 4. When steel casing pipe or carrier pipe is installed under a railway without benefit of a protective coating or is not cathodically protected, the least nominal wall thickness shown in Table 4. Steel casing or carrier pipe installed under a railway shall have a specified minimum yield strength of 2. Mpa or greater. 5. Amend C. S. A. Standard Z6. Clause 4. 8. 3 Crossings of Roads and Railways as follows. Add new item to Clause 4. Cased Crossings. h Casing pipe and joints under railways shall be of leakproof construction capable of withstanding railway loadings specified herein, and shall be of steel unless otherwise indicated herein, or as approved by the Engineer. Replace C. S. A Standard Z6. Clause 1. 2. 4. 6 with the following. Polyethylene carrier pipe may be used in pipeline systems for the transportation of gaseous hydrocarbons under railways if. The design pressure does not exceed 7. Pa. The carrier pipe is made from polyethylene materials permitted by C. S. A. Standard CANCSA B1. R1. 99. 8, and subsequent revisions. The outside diameter of the carrier pipe is not greater than 1. The polyethylene carrier pipe within the entire limits of the railway right of way, is encased in a steel casing pipe meeting the requirements of C. S. A Standard Z6. Replace C. S. A. Standard Z6. Clause 1. 5. 4. 5 with the following. Aluminum pipe is not acceptable for use in pipeline crossings under railways. Requirements for Steam, Water, Sewer and Other Non Flammable Substance Pipelines under Railways. Carrier and Casing Pipe Requirements. Pipelines carrying steam, water other than oilfield steam and water, sewer, and other non flammable or non hazardous substances under railways shall be encased in a larger pipe or conduit called the casing pipe.
Most Popular Pages
- Trang Web Chuyen Crack Game Pc
- Peddlers License St Louis Mo Weather
- Fifa 13 Internal Crack Only Reloaded Tested Meaning
- S Virtual Dj Skins
- Shape File Viewer For Mac
- Sygic Gps Maps Download For Windows Ce
- Install Camera Raw Photoshop Cs5 Portable Download
- Carrier Manual J Calculator
- Download Bollywood Grooves Loops
- Jasc Paint Shop Pro 10 Cracked Servers
- Drivers License Parsing Software Testing